Pockets drainers have stolen $295 million in cryptocurrencies from about 324,000 victims in 2023, Rip-off Sniffer experiences.
In keeping with Rip-off Sniffer’s newest research report, the size of pockets drainer-reported incidents proceed to underscore the severity of the difficulty, with almost $7 million pilfered on Mar. 11 alone. Components such because the USDC depeg and phishing web sites impersonating Circle contributed to this spike, emphasizing the dynamic nature of the assaults, the analysts added.
“Over the previous 12 months, phishing actions have steadily elevated every month with phishing scammers using extra refined techniques to evade safety measures.”
Rip-off Sniffer
The general pattern reveals an alarming escalation within the scale and class of phishing assaults. As famous by Rip-off Sniffer, phishing actions exhibit steady progress, marked by the fast substitute of 1 Drainer with one other as Angel, as an example, seems to be the successor to Inferno Drainer, a malware that pilfered over $80 million in simply 9 months in 2023.
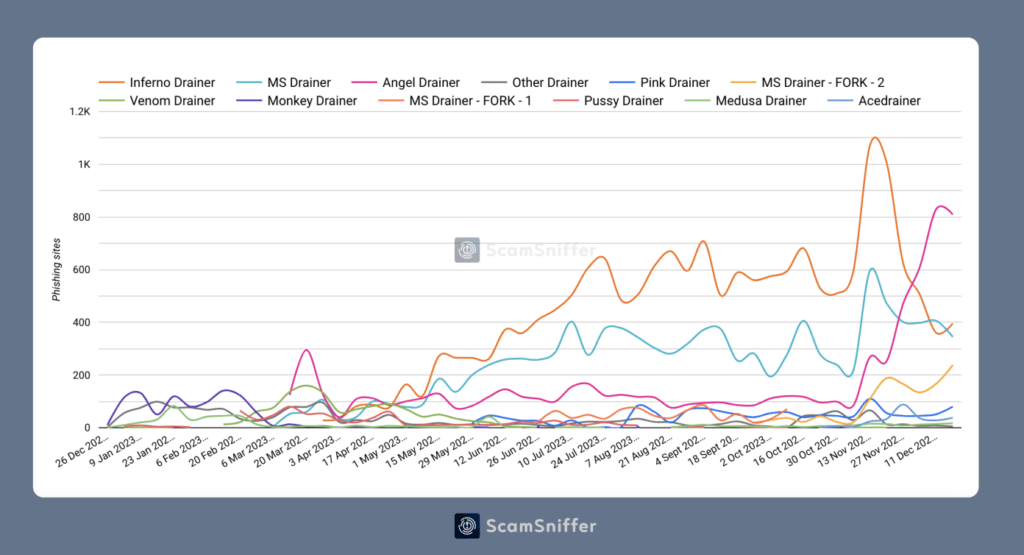
In keeping with the analysts, phishing assaults make use of varied schemes centered on signing strategies, which grant dangerous actors particular rights to empty cryptocurrencies from both digital wallets or good contracts. Among the many 13 most extreme incidents, experiencing cumulative losses of $50 million, victims often suffered from scammers signing such approvals as Improve Allowance, Improve Approval, ERC20 Allow, Approve, and others.
In whole, Rip-off Sniffer recognized virtually 145,000 malicious URLs in 2023. Regardless of some drainers going darkish, new ones maintain changing them, illustrating the persistent problem posed by these malicious actors.

