Binance’s supply code has been overtly accessible on a GitHub repository for months, with the change asserting that the leak posed solely a ‘negligible threat.’
Journalists at 404 Media discovered what they are saying is a “extremely delicate cache of code, infrastructure diagrams, inner passwords,” and different technical data associated to Binance, overtly obtainable on a GitHub repository for a number of months.
In line with the report, the repository included a folder labeled ‘binance-infra-2.0’ with a diagram illustrating the interconnections amongst varied parts of Binance’s dependencies. Moreover, it contained quite a few scripts and code, a few of which appeared associated to Binance’s implementation of passwords and multifactor authentication, with feedback in each English and Chinese language, as famous by 404 Media.
Whereas a spokesperson for Binance confirmed the leak, noting that the knowledge “posed a negligible threat to the safety of our customers, their property or our platform,” the outline of the takedown request confirmed a barely completely different image, saying that the code “poses a big threat to Binancec. and causes extreme monetary hurt to Binance and person’s confusion/hurt.”
The spokesperson additionally added that the code “doesn’t resemble what we presently have in manufacturing.”
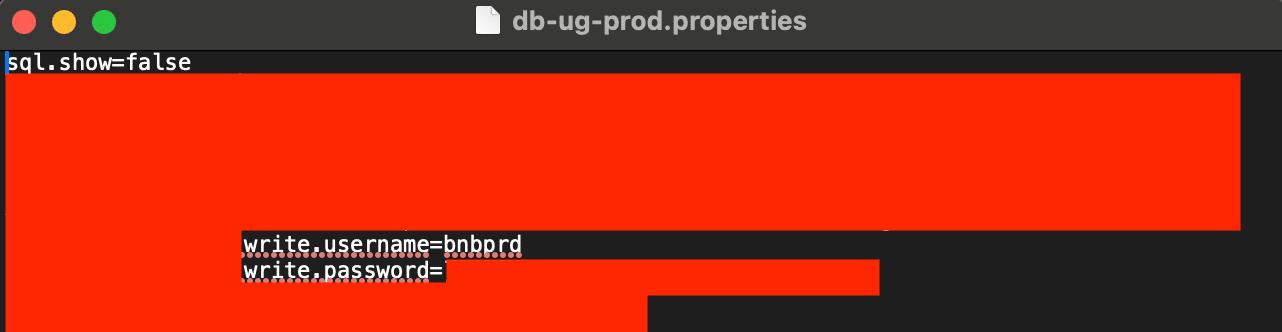
As per the report, the leak contained passwords for programs marked as “prod,” indicating manufacturing programs relatively than demo or improvement environments. Moreover, a minimum of two of those passwords corresponded to Amazon Net Companies’ servers utilized by Binance, the report says. Nevertheless, it’s unclear if a 3rd occasion distributed the code maliciously or if a Binance worker by accident uploaded it to GitHub.

